PrismaKubernetesInit ContainersDatabase MigrationsDeploymentDockerContainerizationDevopsBackend
Running Prisma Migrations the Right Way
A quick look at a better way to handle database migrations in containerized environments. By using Kubernetes Init Containers, you can ensure your database schema is always ready before your application starts, making your deployments more robust.
3 min read
274 views
A Quick Look at a Better Way to Handle Database Migrations in Containerized Environments
My journey into Kubernetes has been a fascinating one, filled with "aha!" moments. Recently, as I was preparing to deploy a backend application that uses Prisma, I encountered a common challenge: how do I run my database migrations before the backend service starts?
My initial thought was to simply modify my package.json file. Something like this:
"start": "npx prisma migrate deploy && node dist/index.js"
This works perfectly well in development. The migration runs, and if it succeeds, the application starts. If it fails, the process stops. Simple, right? But in a production Kubernetes cluster, this approach felt a little too... fragile. What if the database wasn't ready when the command ran? What if the container restarted for some reason?
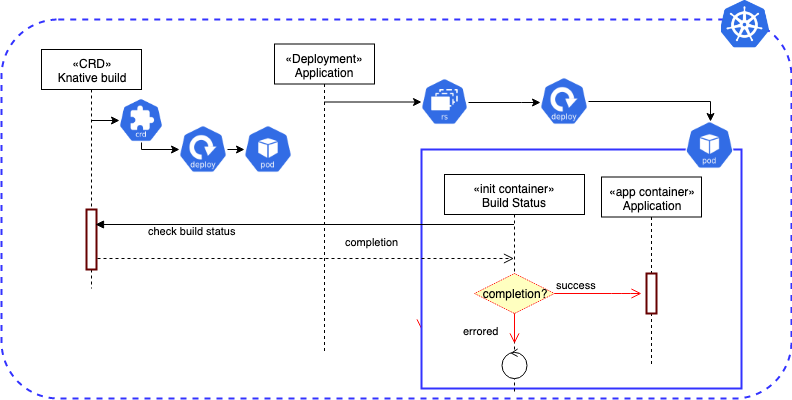
This is where I discovered one of Kubernetes' most elegant features: Init Containers.
What Are Init Containers?
An Init Container is exactly what it sounds like: a container that runs to completion before any of your main application containers start. A Pod can have one or more Init Containers, and they execute in the order they are defined. If any Init Container fails, the entire Pod is restarted, ensuring the pre-flight check or setup is successful.
This is the perfect solution for my Prisma migration problem. I can use an Init Container to run prisma migrate deploy, and my main backend container won't even try to start until the migration is complete and successful.
The Code: A Practical Example
Here’s what my Kubernetes Deployment manifest looks like with the Init Container in place. I'm using the same Docker image for both the Init Container and the main application container, which is a common and efficient practice.
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-backend-deployment
spec:
replicas: 1
selector:
matchLabels:
app: my-backend
template:
metadata:
labels:
app: my-backend
spec:
# The Init Container runs first
initContainers:
- name: prisma-migrate
# Use the same image as your backend application
image: my-backend-image:latest
# Command to run the migrations
command: ["/bin/sh", "-c"]
args:
- npx prisma migrate deploy --schema=./prisma/schema.prisma
# Pass the database connection URL via a secret
env:
- name: DATABASE_URL
valueFrom:
secretKeyRef:
name: database-secret
key: database_url
# Your main backend application container
containers:
- name: my-backend-app
image: my-backend-image:latest
ports:
- containerPort: 3000
initContainers: This new section defines the one-off tasks.
image: I use my-backend-image:latest. Since my Dockerfile bundles the Prisma CLI and the schema, this single image can handle both the migration and serving the application.
command and args: This tells the Init Container to run the prisma migrate deploy command. The --schema flag ensures it's pointing to the correct location.
env: It's crucial that the DATABASE_URL environment variable is available to the migration command. Kubernetes Secrets are the recommended way to handle sensitive information like this.
This pattern is a game-changer for deploying applications with database dependencies. It provides a clean, reliable, and Kubernetes-native way to manage a critical startup task.
By separating the concerns of migration and application startup into different container phases, I've made my deployment more resilient and easier to manage. This is a perfect example of how a deeper understanding of Kubernetes primitives can solve real-world problems more effectively.
Continue Reading
Explore More Articles
Discover more insights about development, DevOps, and technology.
View All Posts